Intune allows us to control which device types can join Microsoft Entra based on the platform they have installed. As we have covered many times previously, there are no technical control silver-bullets in cyber security, however lot’s of small configurations will add up to provide large returns in security posture and a reduction overall in attack surface.
NOTE: If you wish to block personal devices we need to understand how Intune identifies corporate devices, and this can differ dependant on the device type and the Intune enrolment method used. A full explanation is provided here.
Why would we want to do this?
By default all users can join devices to our tenant, and if not restricted this includes personally owned devices. This means that a standard user can enrol their personal device and connect to company resources. We can restrict some of this access via Conditional Access policies, however we can block these devices from being able to enrol in the first place.
How to configure blocking of certain devices.
We head over to the Intune portal at https://intune.microsoft.com/ then go to “Devices” > “Enrolment” > “Device platform restriction”.
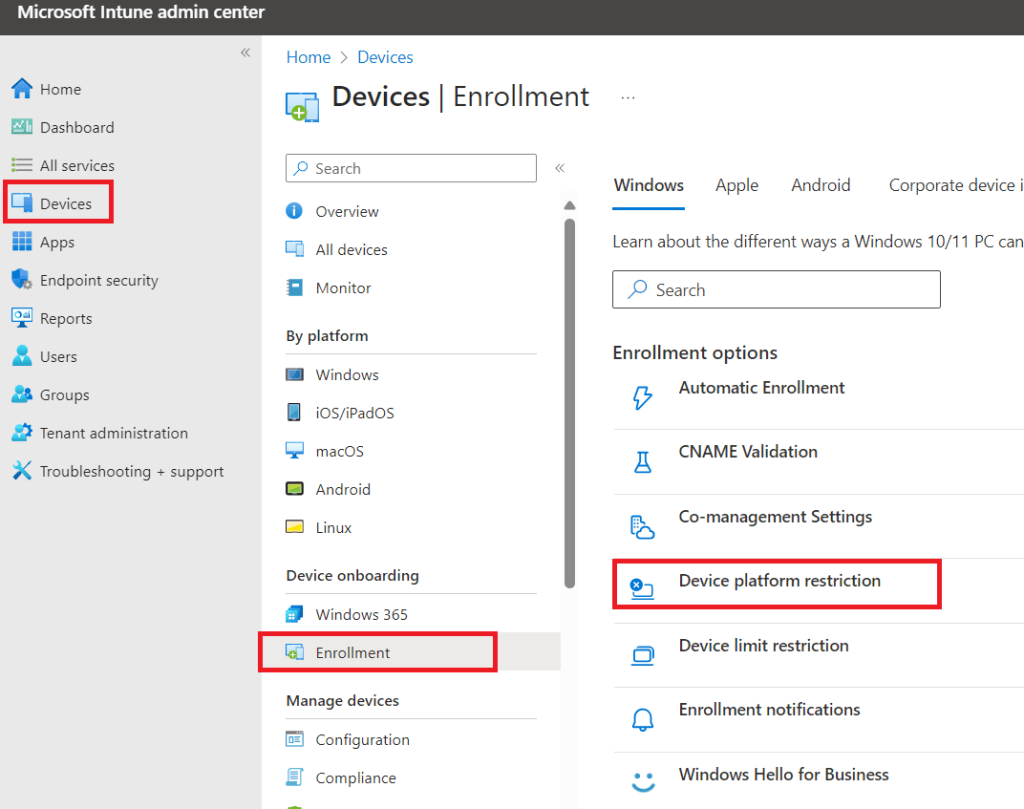
Then select “All Users” as highlighted below.

Then edit platform settings.

Configure as required for our environment. We can see that we have the option to block ALL of a certain platform, or allow corporate owned devices of a certain type, but block personally owned devices of the same type without affecting our organisational devices.
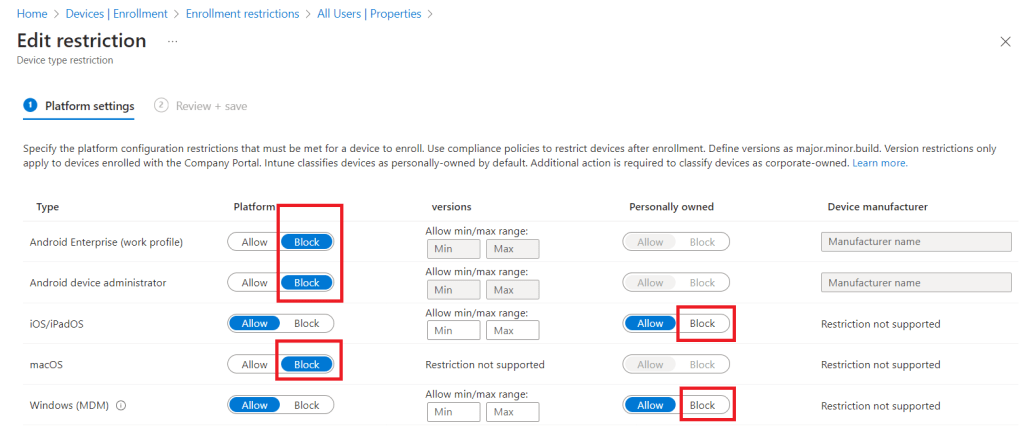
We make our configuration selections, save the changes and exit. Based on the settings in our demo environment shown above, we have blocked all Android and MacOS devices, but have allowed personal and corporate Windows endpoints and iPhones. That’s it nice and simple.
We can force certain prerequisites on these devices and endpoints to ensure they are appropriately secured before being permitted access organisational resources. This is covered elsewhere in this series so we recommend starting at the first guide which starts at enrolment and onboarding before moving onto configurations and hardening.
In the next few guides we will look at Security Baselines, and ASR Rules.
